Then, there are those hackers who just want to exploit, embarrass and expose.
So, which operating systems do you think hackers enjoy exploiting the most?
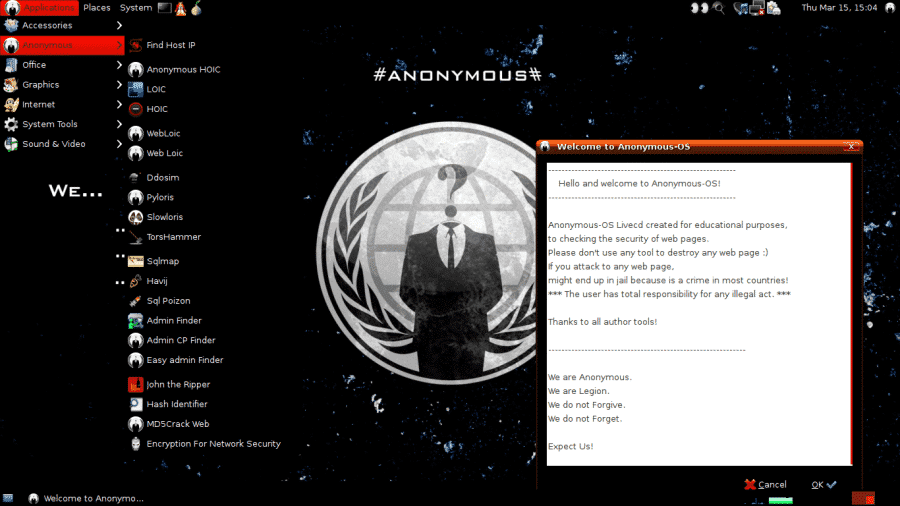
Kali Linux is a Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing.

Kali Linux is an open source project that is installable.
Its geared up both with Windows and Linux-oriented tools.
As such, it introduces a lot of new features and different developing choices.
Parrot uses MATE as a Desktop Environment.
Moreover, the project is available for armel and armhf architectures.
DownloadParrot Security OS
3.
BackBox desktop environment includes a complete set of tools required for ethical hacking and security testing.
BackBox is lightweight OS and requires less hardware specification.
The main aim of BackBox is providing an alternative, highly customizable and well performing system.

The VM contains the best of the open source and free tools that focus on testing and attacking websites.
Its often called the best operating system for Web Penetration Testing.
DownloadSamurai Web Testing Framework
6.
Based on Ubuntu, this Live DVD runs directly from the DVD and doesnt require installation on your hard-drive.
The distribution comes in two forms.
For greater accessibility, there is a Live Hacking menu to help you quickly find and launch the tools.
The second variation is the Live Hacking Mini CD, which is command line only.
The included /lh directory has symbolic links to the different tools included.
It also requires very less hardware requirements.
For example, a fast Pentium 3 or any Pentium 4 class processor (or greater) is sufficient.
For the desktop version, 512MB of memory is required with 1GB recommended.
Further, the command line version just needs 128MB of memory.
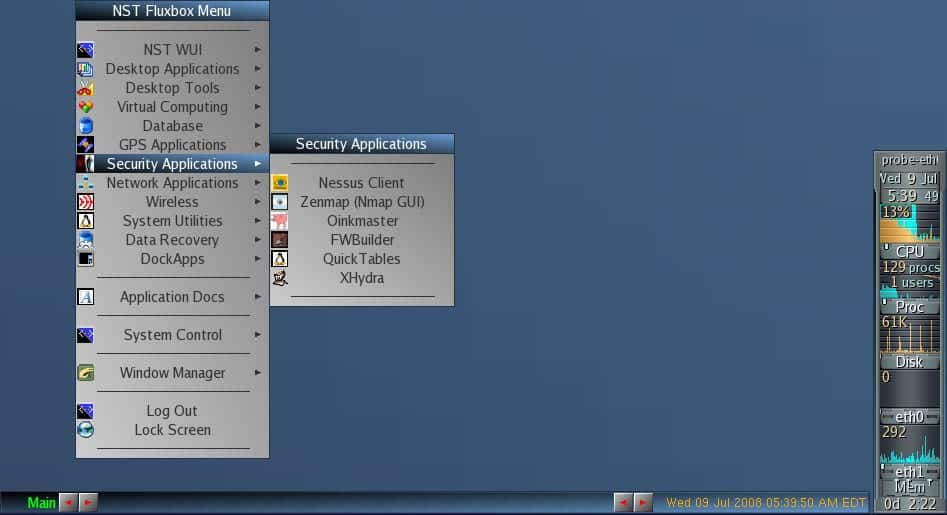
All the majority tools mentioned in the article Top 125 internet Security Tools by Insecure.org are included inside NST.
We can say that NST Control Panel is in a web form.
DownloadNetwork Security Toolkit
8.
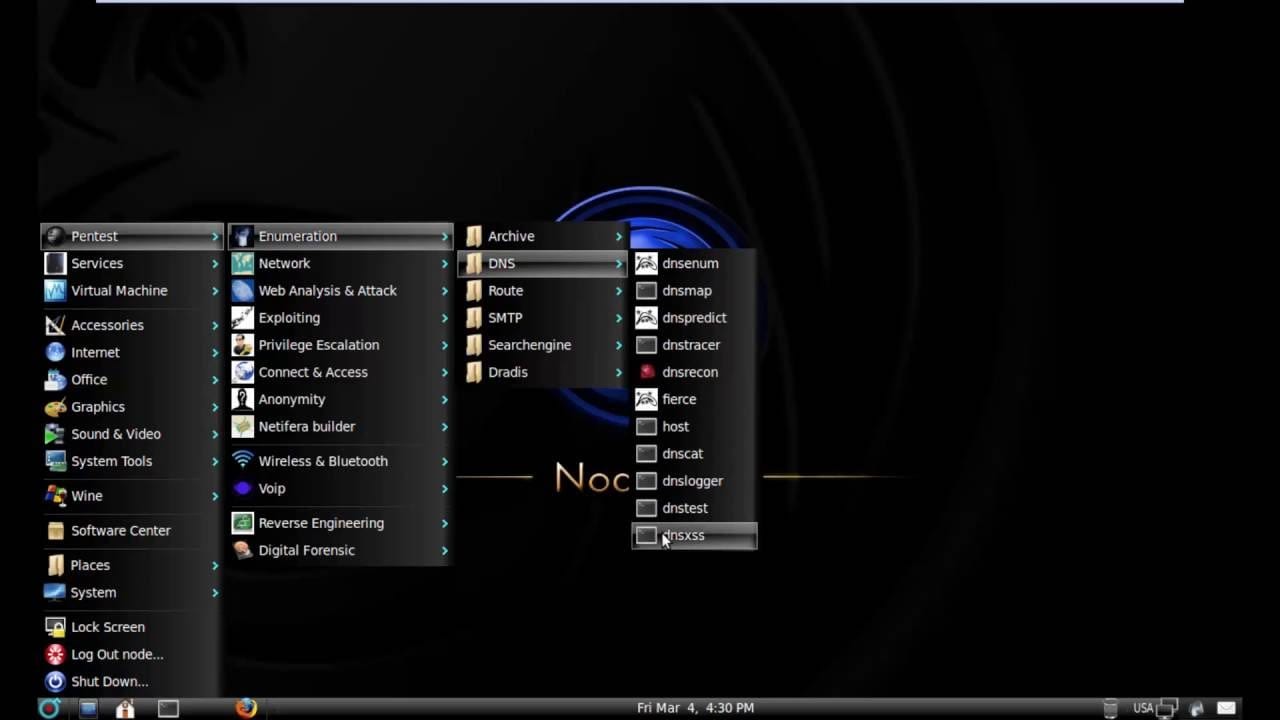
NodeZero uses Ubuntu repositories, so your system will always be up to date.
The system setup is basic and it is primarily designed for disk installation and customization as you want.
Pentoo
Pentoo is a Linux distribution based upon Gentoo Linux.
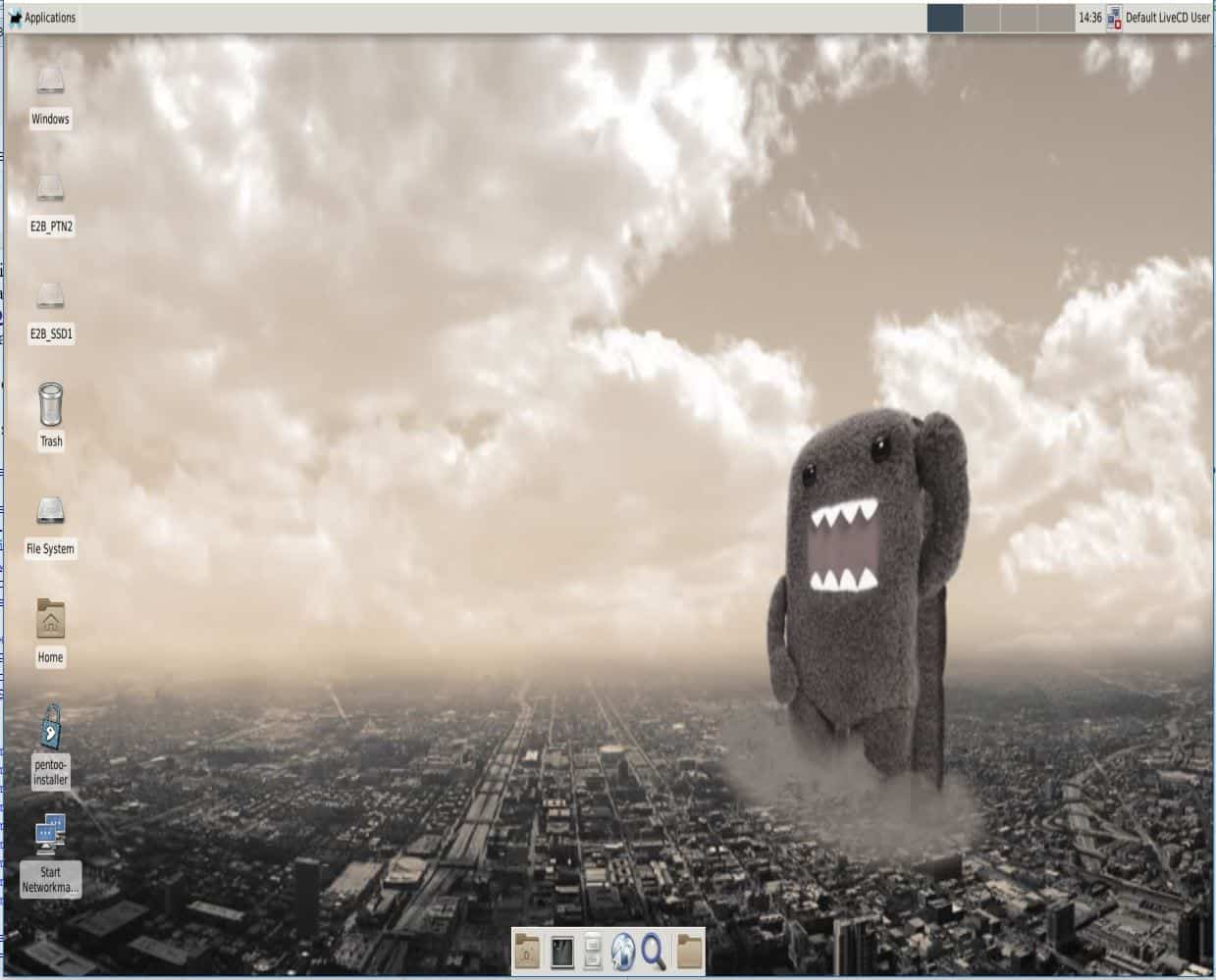
Pentoo can be used as Live CD or Live USB image and the distribution aims at penetration testing.
It is nothing but Gentoo with Pentoo Overlay.
Its basically a Gentoo install with lots of customized tools, customized kernel, and much more.
The newly released distribution is available for both 32-bit as well as 64-bit architecture.
DownloadPentoo
10.Bugtraq
Bugtraq is an electronic mailing list dedicated to issues about computer security.
It is a high-volume mailing list, and almost all new vulnerabilities are discussed there.

It is available in Debian, Ubuntu and OpenSuSe in 32 and 64 bit architectures.
Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time.
source: www.techworm.net