Amidst ransomware threats making headlines in past few weeks a new key in of threat has emerged.
Yes, you have heard it right!
According to the report, its author kept rewriting the malware to prevent detection and enhance its routine.

Over the past few months, we have seen spikes and drops in the number of iterations released.
The latest spike came in mid-April with over 1,200 variants, said the company.
Using multiple devices that run on one platform makes life easier for a lot of people.
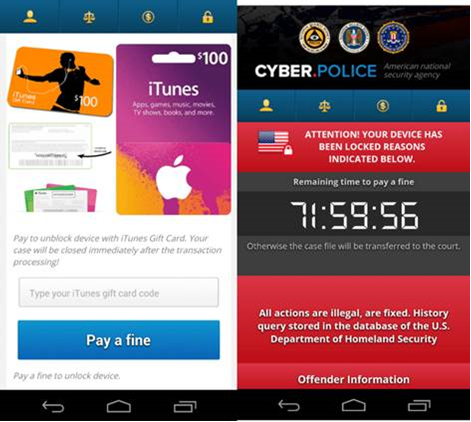
As far as how, its being delivered through standard infection vectors: nothing new or special.
The TVs in this case are accidental collateral damage of the ransomware, and not specifically targeted.
They just happen to be running an attackable version of Android.

There is little difference between FLocker that attacks mobile devices and the version that goes after Smart TVs.
To avoid static analysis, FLocker hides its code in raw data files inside the assets folder.
The file it creates is named form.html and looks like a normal file.

By doing so, the code of classes.dex becomes quite simple and no malicious behavior could be found there.
Thus the malware has the chance to escape from static code analysis.
When the malware runs, it decrypts form.html and executes the malicious code, he wrote.
However, if FLocker detects devices outside these countries, the malware will wait for 30 minutes.
After the short waiting period, it starts the background service which requests gadget admin privileges immediately.
If the user denies the request, it will freeze the screen faking a system update.
FLocker runs in the background and connects to a command and control (C&C).
The ransom webpage fits the screen, irrespective if it infected a mobile gadget or a smart TV.
For those victims who are a little tech savvy, they can possibly handle the task on their own.
He said, Another way of removing the malware is possible if the user can enable ADB debugging.
This kills the ransomware process and unlocks the screen.
Users can then deactivate the rig admin privilege granted to the utility and uninstall the app.
Trend Micro Mobile Security Personal Edition is available on Google Play.
source: www.techworm.net