These flaws could let an attacker attack any system remotely.
The vulnerability in the NTP allows a remote attacker to execute malicious code and take control of victims sytem.
In operation since before 1985, NTP is one of the oldest Internet protocols in use.

NTP was originally designed by David L. Mills of the University of Delaware, who still oversees its development.
This time is maintained by using the NTP protocol.
So we do not need to specify the importance of this protocol.
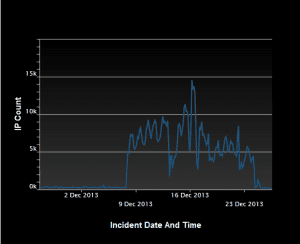
According to the experts, all the versions of NTP prior to 4.2.8 are affected by the flaw.
These vulnerabilities could be exploited remotely.
Exploits that target these vulnerabilities are publicly available.

These flaws have been shown to be very useful in remote attacks, specifically a DDoS attack.
US-CERThas stated that exploitation of these NTP vulnerabilities may allow a remote attacker to execute malicious code.
US-CERT encourages users and administrators to review Vulnerability NoteVU#852879and update to NTP 4.2.8 if necessary.
source: www.techworm.net