Earlier this month, HTC reported its worst quarter in history.
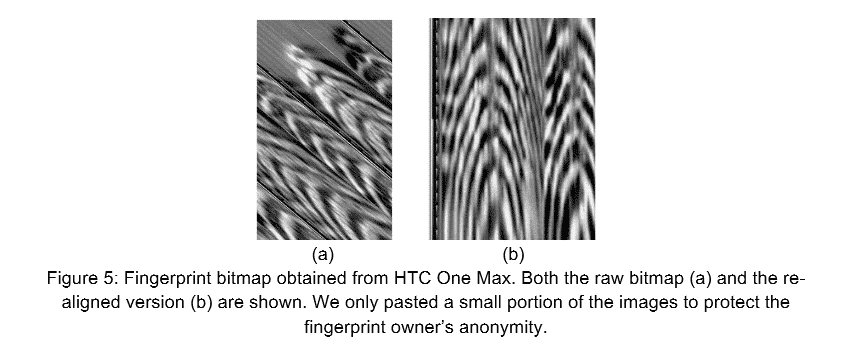
The fingerprints were stored in an image file named dbgraw.bmp in an open, readable and unencrypted folder.
Not all the vendors store the fingerprints securely.

One example is HTC One Max XX the fingerprint is saved as /data/dbgraw.bmp with 0666 permission (worldXreadable).
The FireEye team also added Any unprivileged processes or apps can steal a users fingerprints by reading this file.
As a result, a malicious process could steal multiple images without detection.
We found that the fingerprint sensor itself in many devices is still exposed to the attackers.
Although the ARM architecture enables isolating critical peripherals from being accessed outside TrustZone (e.g.
by programming the TrustZone Protection Controller), most vendors fail to utilize this feature to protect fingerprint sensors.

Hence, it is impossible to retrieve a scan of the fingerprint.
source: www.techworm.net