Once a system has been infected, a lock screen appears and all files on the equipment are encrypted.
The cyber-security firm first discovered the CoinVault attacks in May 2014.
The CoinVault file-encrypting ransomware program was first documented by Kaspersky researchers in November 2014.
After that raid, the programs authors took a break, as the CoinVault malware campaign proceeded largely undeterred.
However, they eventually launched a new version called Bitcryptor, a second-generation version of CoinVault.
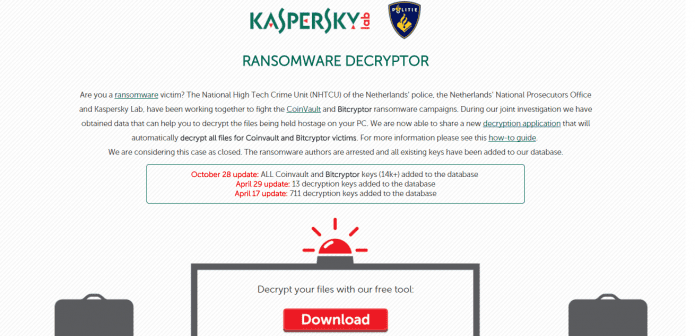
Now, all 14,000 decryption keys are available through Kasperskys ransomware tool.

Researchers say at least 400,000 infection attempts have been made across 49 CryptoWall 3.0 campaigns.
These findings enabled the security firm to publish more than 700 decryption keys in April of this year.
Now Kaspersky has released all 14,000 keys.
We are now able to share a newdecryption applicationthat will automaticallydecrypt all files for Coinvault and Bitcryptor victims.
For more information kindly see thishow-to guide.
We are considering this case as closed.
The ransomware authors are arrested and all existing keys have been added to our database.
Users who believe they have been affected by CoinVault can get into the decryption key directlyhere.
source: www.techworm.net