The added advantage for the criminals is that it effectively circumvents both two-factor authentication and machine identification protections.
IBM Security Trusteer who called it virtual mugging tool, analysed it and has released areportdetailing it.
KL-Remote is distributed by embedding it with other malware and comes preloaded with a list of targeted banking URLs.
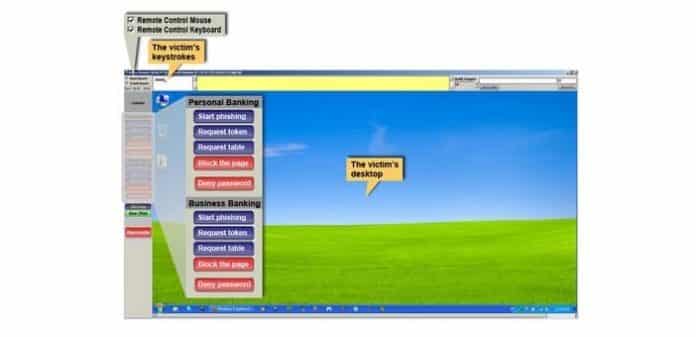
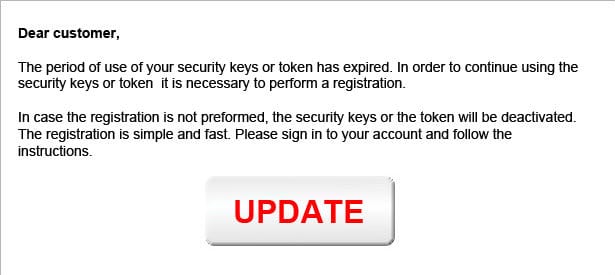
By pushing the Start phishing button, the criminal causes a message to appear on the victims screen.
The tool contains separate messages for each of the targeted banks.
Each message is customized to the banks website login/authentication process and copies its look and feel.
IBM recommends users and financial institutions take the following steps to protect themselves:
Read More


source: www.techworm.net