The researches found the passwords for Telnet access on Google Search and used http access to monitor the communications.
SIM Card vulnerability
SIM cards are vulnerable as per the researchers the numbers is considerably less.
The researchers managed to exploit only 20 of the 100 SIM cards they obtained for testing.

By sending a binary SMS, the researchers managed to lock SIM cards and sniff and decrypt unit traffic.
We dedicated the second part of our research to SIM cards.
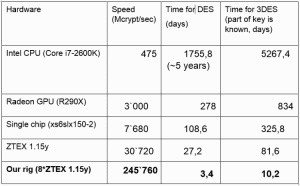
Some you may hack by brute-forcing DES keys.
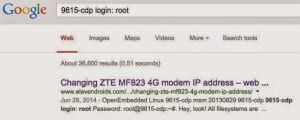
Some respond to an external command without any protection whatsoever and may give out a lot of sensitive information.
It is enough to obtain the key within 3 days.
However breaking the 3DES encryption keys took a tad longer for the researchers.

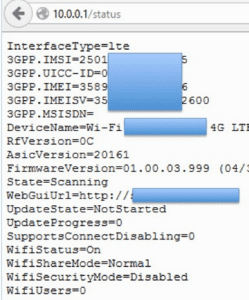
Certain ATMs also deploy these USB modem technologies to remotely transmit payment data.
Video
The video of the presentation they made is given below
Resource :Positive Technologies Blog.

source: www.techworm.net