Many software products use HTTP requests for various features such as software update checking.
These credentials can then be logged by the malicious server.
The credentials are encrypted, but may be brute-forced to break the encryption, the CERT advisory says.

Examples
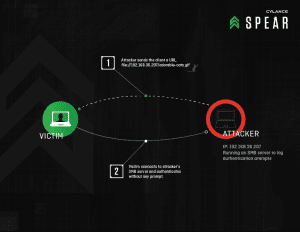
The Cylance researchers have given following examples show different attacks that could be conducted.
to make it effectively demonstrate attack scenarios, the conditions have been simplified.

source: www.techworm.net