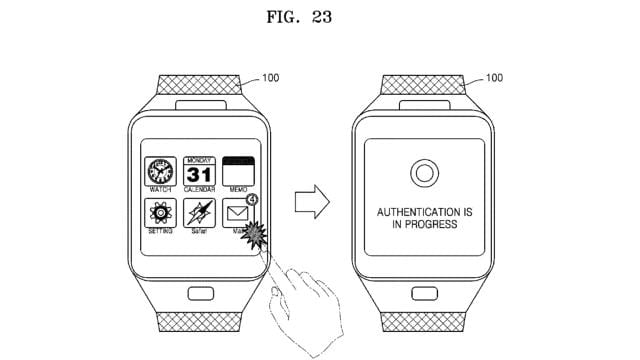
So how will this work?
This will be initiated after the wearable has successfully managed to deduce the identity of the user.
However, what technology will this be advantageous for?

source: www.techworm.net
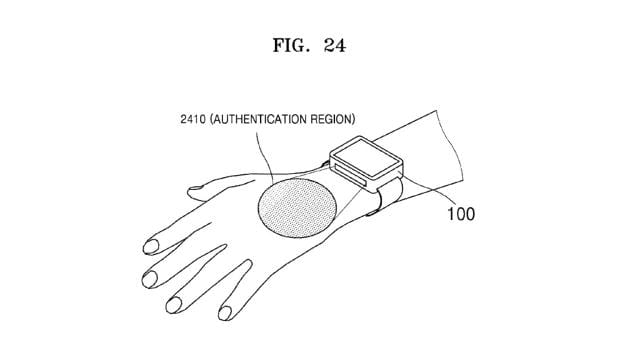
So how will this work?
This will be initiated after the wearable has successfully managed to deduce the identity of the user.
However, what technology will this be advantageous for?



source: www.techworm.net