Obviously, this was not an expected feature of this OS.
The exploitaccordingto HackerHouse works like this:
Registered URL handlers are passed to a command-line utility /usr/bin/nnrurlshow.
Commands will then be executed as arguments when passed to evolution mail.
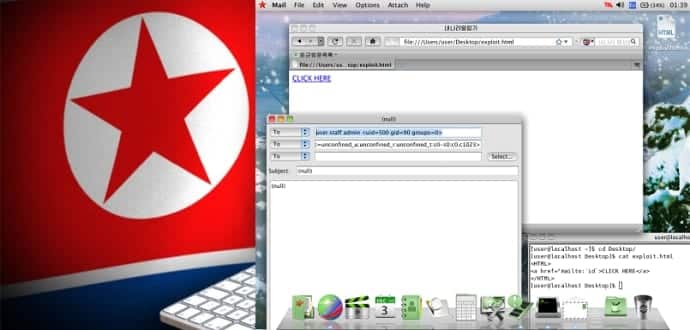
Once the victim clicks the link, all those commands are executed on victims system.
What to expect next?
It is always advisable to go with the well known operating systems to maintain everything in place.

For enthusiasts, a link to images of Red Star OS is provided.
More details, original documentation, and images of Linux based RedStar OS can be foundhere.
source: www.techworm.net