In addition to Tor, the malware was also distributed through pirated softwares hosted on many torrent sites.
Written in assembly language, most MiniDuke files were tiny.
OnionDuke is however, a different family from MiniDuke.
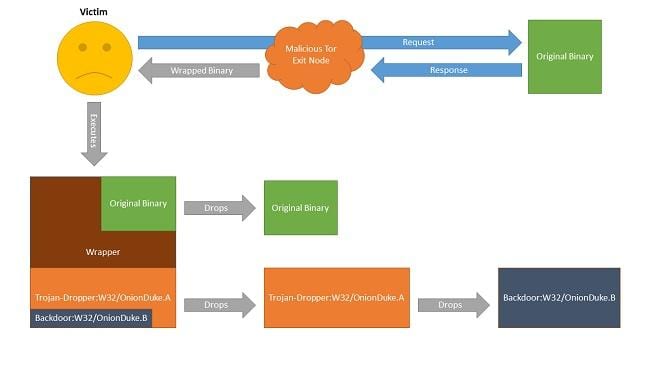
The co-relation was found because both seemed to use the same command & control chain.
From these C&Cs the malware may receive instructions to download and execute additional malicious components.
Another component discovered by F-Secure is theBackdoor:W32/OnionDuke.A.

which contains the domains of the command and control hardcoded within it.
This is what led F-Secure to make the connection to MiniDuke.
Attackers also believe that Twitter is also being used as an addition command channel.
This attack was targeted at mostly Tor users in European countries.
The aim seems to be a country within the sphere of influence of Russia, put bluntly, Ukraine.
The same group also discovered another version of the malware, labelled CosmicDuke.
source: www.techworm.net