The listed Samsung devices are available for use with classified government networks and data.
All devices and capabilities incorporate security features powered by Samsung KNOX.
Applications and data inside the container are separated.

The DISA Approved Products List may be found at:https://www.disa.mil/Services/web connection-Services/UCCO.
With the iCloud Hacks it was proved that even Celebrities are not safe from hacking.
The Dropbox leaks proved that saving to Dropbox also entails a relatively high risk.
So what do the users do with their images and videos taken in those private moment.
While the US Government thinks so, a security researcher, Eingestellt von Ares doesnt think so.
Infact Ares has demonstrated on his blog as to why Samsungs Knox is vulnerable and quite easily too.

Knox EMM is a enterprise cloud-based management solution for mobile devices which was not part of this analysis.
Looking at the system internals, Knox installs quite a lot of stuff on your phone.
Listing all of them here would be too much.
After a typical Knox installation there are 139 apps and services installed with the prefix com.sec.
- Different files and databases for controls are stored in /data/system/secure_storage and /data/system/container.
A good starting point for Android Apps is the app folder under /data/data/.
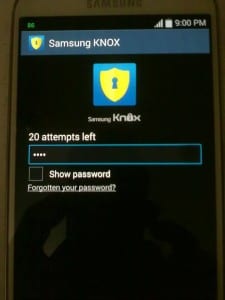
The pin we had to set during the setup of Knox in cleartext!
The other files didnt reveal other interesting stuff.
But back to the pin.xml file.
What is the purpose of the pin in Knox anyway?
But there is a small button under the textfield called Password forgotten?.
By tapping it, you have to provide your pin.
- the original length of your password!).
So now it is pretty obvious that Samsung Knox is going to store your password somewhere on the gadget!
The content is a crypted string: 72C9EE6D56CB15916A4CAB01814F978FA1E2689D (I modified the string for obvious reasons ;)).
So this looks like an AES encrypted string.
The method getKeyForPassword is placed in a C written shared library called mealy.
The method getPartialString substractes a part out of the Android ID.
Samsung really tried to hide the functionality to generate the key, following the security by obscurity rule.
For such a product the password should never be stored on the rig.
There is no need for it, only if you forget your password.
Android is using a PBKDF2 function from the encryption password you choose and never persists it on the machine.
Resource :Mobile Security Blog
Read More
source: www.techworm.net