In other words, the attack technique depends on the basic echo principle of sonar systems.
How does the SonarSnoop attack work?
SonarSnoop uses FingerIO as the primary source of inspiration and is the malicious version of FingerIO.
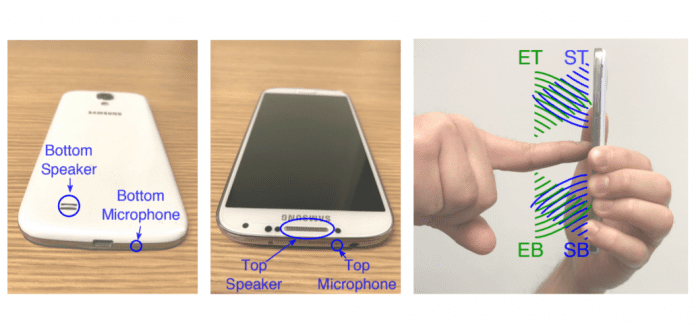
Combining observed movement from multiple microphones allows us to estimate strokes and inflections, the researchers explained.
Thanks to the ML algorithms built into the attack.
The research team used 12 unlock patterns with 15 unique strokes in their experiment.

Also Read-Hackers can spy on your gear screens through the webcam microphone
Read More
source: www.techworm.net